01
Discover
We run collaborative workshops with your team to understand requirements, define goals, and build a prioritized backlog for automation initiatives.
Output: Automation initiative backlog
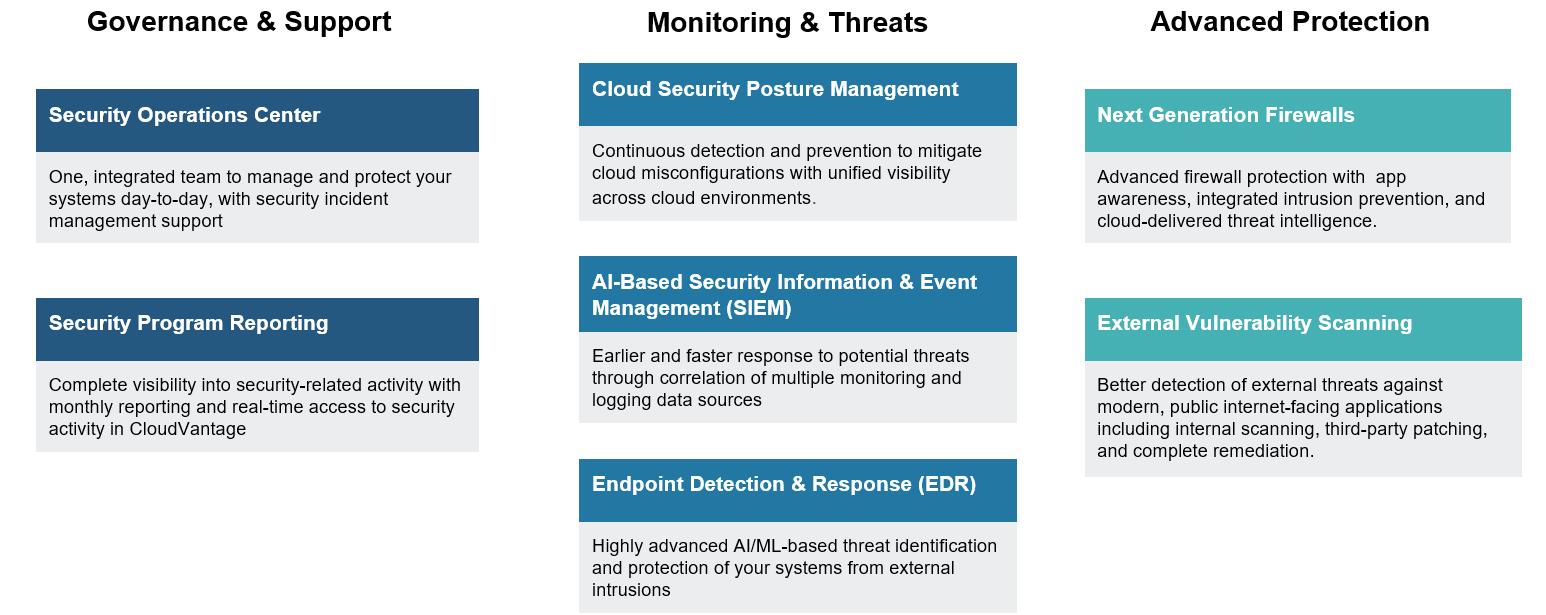
Combining leading edge tools, rigorous processes, and our expert security team, we have embedded cybersecurity throughout our service delivery. Our integrated SecOps model includes advanced AI/ML-based threat identification, protection from external intrusions, and rapid response to potential threats. Backed by a 24x7 Security Operations Center, end-to-end alerting on anomalous behavior protects your cloud ecosystem from security risks.
average cost of a breach
(Help Net Security)
breaches caused by human error
(Trustle.com)
days to identify & contain a breach
(IBM)
End-to-end protection & governance of your critical workloads.
Continuous protection against the #1 vector for ransomware by alerting users in real time and providing 24/7 expert triage.
Extends Security Program Reporting with assessment of your security program health to improve program effectiveness, including Firewall Governance.
Extends endpoint detection & response to proactively hunt for threats in your environments and network (NDR).
Comprehensive, AI-powered protection across identities, endpoints, data, apps, and infrastructure, reducing complexity while enhancing security posture.
Provides credentialed vulnerability scanning on systems to eliminate vulnerabilities at a host level. Protera collaborates with client team to remediate.
Enhanced protection for modern web-based applications against sophisticated attacks such as cross-site scripting (XSS).
We run collaborative workshops with your team to understand requirements, define goals, and build a prioritized backlog for automation initiatives.
Output: Automation initiative backlog
Our team executes against the jointly-defined backlog using an agile, sprint-based approach to quickly deliver incremental value with visibility into progress.
Output: Automation enabled via agile delivery model
Regular sessions to review progress, reprioritize tasks, and incorporate new requirements for both DevOps automation and operational procedures.
Output: Critical tasks appropriately prioritized

We’re not playing checkers, we’re playing chess. And we’re playing chess at 150 miles per hour, on the internet, with everybody watching. - CJ Moses, CISO, AWS.png?width=800&height=67&name=customer-quote%20(1).png)
Our integrated SecOps model creates a security baseline with continual governance and reporting, augmenting your overall security program and mitigating risk.

Performance of controls that could
impact customers' financial statements.

Performance of controls that provide
assurance to the compliance of the
AICPA cybersecurity compliance
framework.

Adherence to the standard for
Information Security Management
Systems (ISMS). Compliance to the
framework and commitment to pursue
cybersecurity objectives including
information security, risk,
management, and measurement.

Adherence to the framework that
minimizes privacy risks. Compliance
with privacy requirements and
protection of personal information
and comply with laws/regulations.
Schedule a 1:1 conversation with a Protera Security Advisor today.